It is just beyond belief! All this emphasis that's put on security and good practise.......and then we find that someone at the top has left the back door open! ![]()
Part of the problem, I think, is because so many people have fingers in the same pies!
I was enjoying a nice day out on Saturday, so I'm still catching up with the fallout from this (and no doubt that will continue when I return to work tomorrow... ![]() ).
).
Official advice from Microsoft (includes links to security updates for old systems):
Customer Guidance for WannaCrypt attacks
Blog by MalwareTech, the guy who inadvertently activated the malware's "kill switch":
How to Accidentally Stop a Global Cyber Attacks
It's (unsurprisingly) rather technical, but readable and interesting nonetheless. It also helps correct some of the media misreporting during all the panic and confusion. MalwareTech is not an amateur, but an information security professional: his job is to track and stop malware, thus assisting victims and law enforcement. He just happened to be on holiday at the time (his boss has given him another week off to make up for the lost break!).
Also, it looks like the "kill switch" wasn't actually an intentional "kill switch" (self-destruct mechanism) after all: current thinking is that it was a badly-engineered attempt by the bad guys to try to prevent the good guys analysing the malware. In theory, the bad guys' thinking was valid (and has been done before), but in practise its poor implementation provided the good guys with a simple way of stopping it altogether (even if they didn't initially realise it).
Eugene's Lair posted:I was enjoying a nice day out on Saturday, so I'm still catching up with the fallout from this (and no doubt that will continue when I return to work tomorrow...
).
Official advice from Microsoft (includes links to security updates for old systems):
As EL's post says the above link includes links to patches for older versions of Windows including Windows XP. Microsoft have taken this rare step due to the widespread problems. Micosoft also says that Windows 10 users were not targeted in Friday's attack.
its ok in wales..cos they got superior IT..NHS Wales is run by Labour..
El Loro posted:Eugene's Lair posted:I was enjoying a nice day out on Saturday, so I'm still catching up with the fallout from this (and no doubt that will continue when I return to work tomorrow...
).
Official advice from Microsoft (includes links to security updates for old systems):
As EL's post says the above link includes links to patches for older versions of Windows including Windows XP. Microsoft have taken this rare step due to the widespread problems. Micosoft also says that Windows 10 users were not targeted in Friday's attack.
I'm on 8.1 but I keep it updated as soon as they come out ![]() Usually every second Wednesday in the month unless it's something that is urgent
Usually every second Wednesday in the month unless it's something that is urgent ![]()
I thought hubby was keeping all our computers updated. Just run a check and the last one was September 2015. ![]()
I've just updated it all now - 54 updates!
Extremely Fluffy Fluffy Thing posted:I thought hubby was keeping all our computers updated. Just run a check and the last one was September 2015.
I've just updated it all now - 54 updates!
![]()
2 more have appeared!
Extremely Fluffy Fluffy Thing posted:2 more have appeared!
![]()
Make sure you reboot your machine to fully complete any updates, and then check that there aren't any other updates pending.
I find it a good idea to do the same thing when manually updating my anti-virus software: do an update, then keep attempting to update again until it comes back with a "not required" message (or equivalent).
(As an illustration: I've just gone and attempted a manual update to my anti-virus software, and although it last did an automatic update only 4 hours ago, there were 4 updates waiting! ![]() I think we can presume that the anti-virus guys are being kept very busy at the moment...
I think we can presume that the anti-virus guys are being kept very busy at the moment... ![]() )
)
Have done all that Eugene. And again this morning!
Not too surprisingly when we got into work this morning there were notices on all the computers saying "DO NOT SWITCH ON!"
Some folk got their computers back mid-m0rning, but I didn't get mine back until mid-day and even then it was a bit unstable and all its functions weren't readily available. There were workarounds to access some apparently 'missing' stuff, but it was a real pain!
Extremely Fluffy Fluffy Thing posted:Not too surprisingly when we got into work this morning there were notices on all the computers saying "DO NOT SWITCH ON!"
Some folk got their computers back mid-m0rning, but I didn't get mine back until mid-day and even then it was a bit unstable and all its functions weren't readily available. There were workarounds to access some apparently 'missing' stuff, but it was a real pain!
![]()
Interesting comparison...
Sophos are a major software security company, who have the NHS amongst their clients. Here are screen shots of how Sophos publicly portrayed their relationship with the NHS before (top) and after (bottom) the WannaCrypt attack:
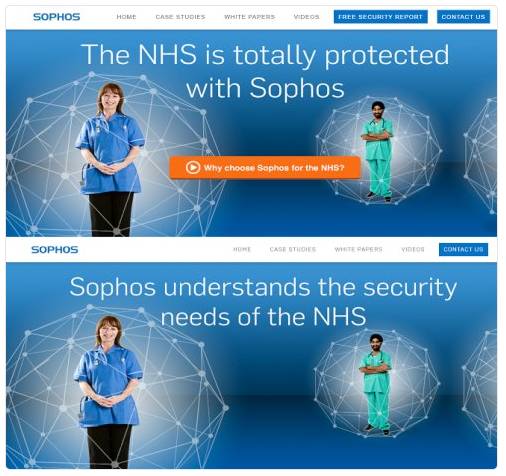
![]()
Eugene's Lair posted:Interesting comparison...
Sophos are a major software security company, who have the NHS amongst their clients. Here are screen shots of how Sophos publicly portrayed their relationship with the NHS before (top) and after (bottom) the WannaCrypt attack:
That's a bit worrying - our company (some months ago) asked if we'd mind installing Sophos on our home computers to maintain security of the company system (we'll often log in from home) I've been relying on that as an a/v - maybe i should get something else?
Kaffs posted:Eugene's Lair posted:Interesting comparison...
Sophos are a major software security company, who have the NHS amongst their clients. Here are screen shots of how Sophos publicly portrayed their relationship with the NHS before (top) and after (bottom) the WannaCrypt attack:
That's a bit worrying - our company (some months ago) asked if we'd mind installing Sophos on our home computers to maintain security of the company system (we'll often log in from home) I've been relying on that as an a/v - maybe i should get something else?
I've not used Sophos products before, but they're supposed to have a good reputation, and I've used their guides in the past for Facebook settings, etc.
The main point about these "before and after" shots is that they were essentially making claims of 100% security, which simply isn't realistic and may well have led to complacency. General feeling seems to be that in this case, they've over-sold their product and underestimated the problem.
The full Register article I got this from can be found here.
Police anti-ransomware warning is hotlinked to 'ransomware.pdf'
'Official anti-ransomware advice issued by [Metropolitan and City of London] police to businesses can only be read by clicking on a link titled "Ransomware" which leads direct to a file helpfully named "Ransomware.pdf".'
Oh dear... ![]()
Eugene's Lair posted:Police anti-ransomware warning is hotlinked to 'ransomware.pdf'
'Official anti-ransomware advice issued by [Metropolitan and City of London] police to businesses can only be read by clicking on a link titled "Ransomware" which leads direct to a file helpfully named "Ransomware.pdf".'
Oh dear...
![]() Oh dear indeed Eugene
Oh dear indeed Eugene ![]()
![]()
Eugene's Lair posted:Police anti-ransomware warning is hotlinked to 'ransomware.pdf'
'Official anti-ransomware advice issued by [Metropolitan and City of London] police to businesses can only be read by clicking on a link titled "Ransomware" which leads direct to a file helpfully named "Ransomware.pdf".'
Oh dear...
Bit of a clanger ![]()
It turns out that the majority of computers affected were running Windows 7 rather than Windows XP.
http://www.bbc.co.uk/news/technology-39997581
Today is the first day since the attack that we have been able to print labels. The IT guys are applying various patches, so we have been told not to switch off our computers ALL this week. The layout of the screens keep changing, our icons are waltzing about and occasionaly go AWOL! ![]()
A hacking group closely tied to North Korea was behind the massive WannaCry attack earlier this month, security company Symantec says.
The way the attack was set up made it "highly likely" that the Lazarus group was responsible, it said.
Lazarus has been blamed for a 2014 attack on Sony and the theft of $81m (£62m) from Bangladesh's central bank.
In those attacks, the group is believed to have worked on behalf of North Korea's government.
Today at work we received an e-mail urging us all to be extra vigilant over the heightened terrorist threat and giving some guidelines as to what to be wary off and how to report any suspicions we may have!
